The Problem
The hamsters have triumphed! We found an open Github repository! It looks like some sort of game; perhaps they’re planning to trick our humans into playing it. We need to know if there’s any data hidden in the game that might harm our humans.
Note: You’ll need to prepend “flag-” to the flag.
- https://squarectf.com/challenges/the-turing-agent
The github repo in the link above contains the following files:
4.0K drwxr-xr-x 3 cpacho users 4.0K Oct 6 13:29 ..
4.0K drwxr-xr-x 3 cpacho users 4.0K Oct 6 11:29 .
4.0K -rw-r--r-- 1 cpacho users 1.4K Oct 6 10:11 bighint.txt
4.0K drwxr-xr-x 8 cpacho users 4.0K Oct 6 10:11 .git
32K -rw-r--r-- 1 cpacho users 32K Oct 6 10:11 mission.gb
4.0K -rw-r--r-- 1 cpacho users 1.7K Oct 6 10:11 README.txt
4.0K -rw-r--r-- 1 cpacho users 804 Oct 6 10:11 smallhint.txt
4.0K -rw-r--r-- 1 cpacho users 713 Oct 6 10:11 tools.txt
The challenge was located in mission.gb, a gameboy ROM. To start, install visualboyadvance from the kali repos and load up mission.gb. Once the gameboy rom is loaded up, it asks for a code. The code is 16 digits and can contain “UP”, “DOWN”, “LEFT”, “RIGHT”, “A”, or “B”.


Entering an invalid code will result in a failure message of “NO GOOD.”

The Solution
Loading the binary in radare2 (r2 -A mission.gb) and looking at the file’s strings was very useful. The following strings seemed important:
vaddr=0x00002bf8 paddr=0x00002bf8 ordinal=122 sz=8 len=7 section=rombank00 type=ascii string=I'M IN.
vaddr=0x00002c1b paddr=0x00002c1b ordinal=123 sz=9 len=8 section=rombank00 type=ascii string=NO GOOD.
The success string (I’M IN) is called within function fcn.00002b26 and the failure string is called within fcn.00002c00. The goal is to land in the success function. The success/failure functions are only called in one place in the binary.
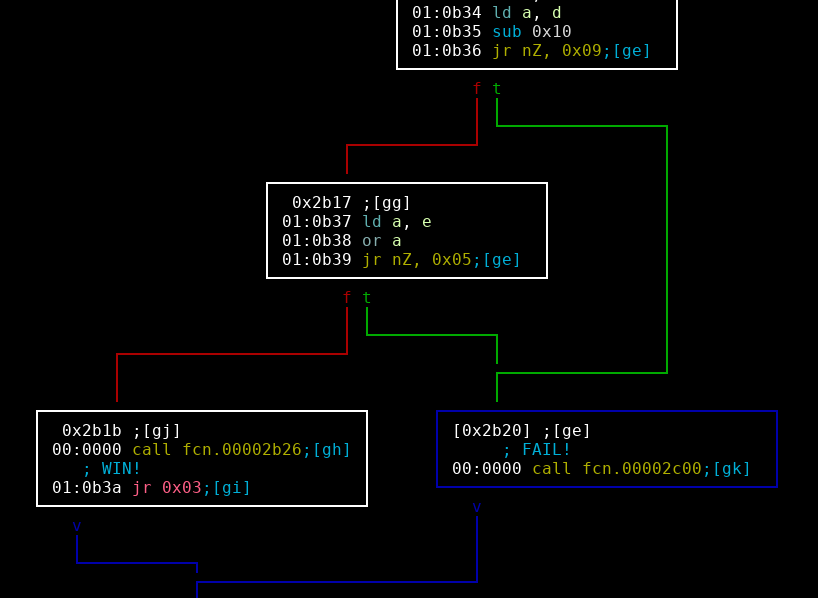
There are two conditional statements that need to be traversed before entering the WIN or FAIL functions. Nop out the two compares (0x00002b15 & 0x00002b19), and that will lead directly to the WIN function!
0x00002b0b 361e ld [hl], 0x1e
0x00002b0d f800 ld hl, sp + 0x00
0x00002b0f 56 ld d, [hl]
0x00002b10 1e00 ld e, 0x00
0x00002b12 7a ld a, d
0x00002b13 d610 sub 0x10
0x00002b15 00 nop
0x00002b16 09 add hl, bc
0x00002b17 7b ld a, e
0x00002b18 b7 or a
0x00002b19 00 nop
0x00002b1a 05 dec b
0x00002b1b cd262b call fcn.00002b26
Now, the following will appear when the patched gameboy rom is opened:


